# tethered downgrade / jailbreak for checkra1n devices
thanks iSuns9 for translation!
Caution: This is just a trick. There might be some insufficiencies and it might not work for iOS versions that are not very close.
requirements: any iOS 14.x (or less?) SHSH blob
# STEP 1
apply patches to /usr/sbin/asr and /usr/local/bin/restored_external inside the restore ramdisk.
- iSuns9's restored_external64patcher
- exploit3dguy's asr64_patcher
# STEP 2
apply kernel patches (amfi).
- iSuns9's fork Kernel64Patcher
# STEP 3
make modifications to the IPSW.
This is a well known technique to people who know downgrades that use odysseus(32) and/or an iBoot exploit. replace the LLB, iBoot etc. in the Firmware/all_flash folder of the IPSW with the ones that match your SHSH blobs. Further, if this creates conflicts with the Firmware you're restoring to, make according adjustments to the Buildmanifest. Please refer to odysseus' documentation for detailed information.
By doing this the device will boot into recovery mode instead of staying in DFU mode after the restore process.
# STEP 4
restore the custom firmware using futurerestore.
- futurerestore
- 0x7ff's gaster
Enter pwned DFU mode before attempting to restore with futurerestore.
MBP:~ user$ ./gaster pwn
MBP:~ user$ ./futurerestore -t ticket.shsh2 --latest-baseband --latest-sep --use-pwndfu --no-cache --skip-blob --rdsk custom_ramdisk.im4p --rkrn patched_kernel.im4p custom.ipsw
After the restore is finished the device will be in Recovery Mode.
# STEP 5
boot using checkra1n
Caution: the current version of checkra1n (v0.1.12.4) is only functional on devices that run a (properly signed) iBoot from iOS 14 and below. In other words if you don't fulfill the aforementioned requirement of having valid iOS 14 SHSH blobs for your device, you won't be able to use this method.
We want to tetherboot our device with checkra1n but PongoOS won't boot without any changes. checkra1n's bootchain only works on devices with properly signed boot files but not on devices that have been downgraded tethered. But because we have a properly signed iBoot, it's possible to boot until the stage 2 KJC Loader. Because the patches for stage 2 and up are already open source we can take a look at them.
- checkra1n's pongoOS
The main hindrance at this point is that we don't have valid signatures for firmware files like the kernel and Devicetree. Therefore by just adding patches for skipping signature verification when PongoOS patches iBoot, we can properly boot PongoOS.
We can make checkra1n load an arbitrary PongoOS file using the -k parameter.
MBP:~ user$ /Applications/checkra1n.app/Contents/MacOS/checkra1n -k path/to/pongo.bin
After PongoOS has booted we can execute KernelPatchFinder like usually and that way we can boot a tethered downgraded device into a jailbroken state with checkra1n.
# DEMO
I'm downgrading an iPhone 6S(n71ap) to iOS 14.3 tethered using iOS 14.8 SHSH blobs.
This is a demo on the iPhone 6S. Other devices might require additional measures.
# requirements
- libdmg-hfsplus
- img4lib
- ldid
- asr64_patcher
- restored_external64_patcher
- Kernel64Patcher
- kerneldiff.py
- gaster
- futurerestore
- pongoOS
- checkra1n
# steps for creating the custom firmware
# extracting the IPSW
unzip iPhone_4.7_14.3_18C66_Restore.ipsw -d custom/
unzip iPhone_4.7_14.8_18H17_Restore.ipsw -d temp/
# moving the DeviceTree
mkdir custom/Downgrade/
mv custom/Firmware/all_flash/DeviceTree.n71ap.im4p custom/Downgrade/
mv custom/Firmware/all_flash/DeviceTree.n71map.im4p custom/Downgrade/
# replacing the contents of the Firmware/all_flash folder with the ones from iOS 14.8
rm -r custom/Firmware/all_flash/
mv temp/Firmware/all_flash/ custom/Firmware/
sudo rm -r temp/
# re-moving the DeviceTree
rm custom/Firmware/all_flash/DeviceTree.n71ap.im4p
rm custom/Firmware/all_flash/DeviceTree.n71map.im4p
mv custom/Downgrade/DeviceTree.n71ap.im4p custom/Firmware/all_flash/
mv custom/Downgrade/DeviceTree.n71map.im4p custom/Firmware/all_flash/
rm -r custom/Downgrade/
# applying patches to files in the RestoreRamdisk
./img4 -i custom/038-83284-083.dmg -o rramdisk.dmg
### ASR
./hfsplus rramdisk.dmg extract usr/sbin/asr asr
ldid -e asr > asr.xml
./asr64_patcher asr asr_p
ldid -Sasr.xml asr_p
./hfsplus rramdisk.dmg mv usr/sbin/asr usr/sbin/asr_o
./hfsplus rramdisk.dmg add asr_p usr/sbin/asr
./hfsplus rramdisk.dmg chmod 0755 usr/sbin/asr
rm asr asr_p asr.xml
### restored_external
./hfsplus rramdisk.dmg extract usr/local/bin/restored_external restored_external
ldid -e restored_external > restored_external.xml
./restored_external64_patcher restored_external restored_external_p
ldid -Srestored_external.xml restored_external_p
./hfsplus rramdisk.dmg mv usr/local/bin/restored_external usr/local/bin/restored_external_o
./hfsplus rramdisk.dmg add restored_external_p usr/local/bin/restored_external
./hfsplus rramdisk.dmg chmod 0755 usr/local/bin/restored_external
rm restored_external restored_external_p restored_external.xml
./img4 -i rramdisk.dmg -o custom_ramdisk.im4p -A -T rdsk
rm rramdisk.dmg
# patching the RestoreKernelCache
./img4 -i custom/kernelcache.release.n71 -o kc
./Kernel64Patcher kc pwnkc -a -f
touch kc.bpatch
python3 kerneldiff.py kc pwnkc
./img4 -i custom/kernelcache.release.n71 -o patched_kernel.im4p -T rkrn -P kc.bpatch
rm kc pwnkc kc.bpatch
# UPDATE: patching the KernelCache
This should normally be done from PongoOS but as a proof of concept we're applying this patch directly to the KernelCache.
This is necessary when using unsigned AOP firmware etc.
mv custom/kernelcache.release.n71 custom/orig_kernelcache.release.n71
./img4 -i custom/orig_kernelcache.release.n71 -o kc
./Kernel64Patcher kc pwnkc -f
touch kc.bpatch
python3 kerneldiff.py kc pwnkc
./img4 -i custom/orig_kernelcache.release.n71 -o custom/kernelcache.release.n71 -T krnl -P kc.bpatch
rm kc pwnkc kc.bpatch
# zipping everything
cd custom/
zip -r0 ../custom.ipsw *
cd ..
# steps for the Restore
# restoring the custom IPSW using futurerestore
./gaster pwn
./futurerestore -t ticket.shsh2 --latest-baseband --latest-sep --use-pwndfu --no-cache --skip-blob --rdsk custom_ramdisk.im4p --rkrn patched_kernel.im4p custom.ipsw
# steps for booting the device
It's necessary to also patch out signatures checks when PongoOS applies its iBoot patches. I currently don't have an easy way to do this but on the iPhone 6S with an iOS 14.8 iBoot you can patch it as follows:
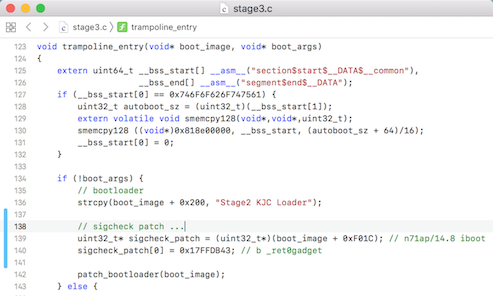
booting this modified PongoOS with checkra1n
Connect the device in Recovery Mode via USB, execute the following command and follow the instructions on the screen:
/Applications/checkra1n.app/Contents/MacOS/checkra1n -k pongo.bin
After PongoOS has booted you can transfer the kpf/ramdisk of checkra1n v0.12.4 to the device using ra1npoc's pongoterm and boot them.
./pongoterm -r